Continuously Manage and Reduce Exposures Across Your Attack Surface
Your attack surface changes daily and one-time testing can’t keep up. That’s why we deliver continuous testing and validation to find and fix exposures before attackers can exploit them.

Penetration Testing as a Service (PTaaS)

Dark Web Analysis

DevSecOps as a Service

Managed SIEM & Purple Teaming

Reduce Risk
Continuously identify and reduce exposures with testing that spans your entire attack surface.

Consolidate Tools
Reduce costs and increase efficiency with a platform that replaces toolsets and integrates broadly.

Streamline Compliance
Easily meet compliance requirements and show proof of testing with complete asset history.
Your Attack Surface Changes Every Day. Your Testing Should Too.
Many organizations still treat security as a periodic task, a compliance checkbox rather than a continuous effort to uncover real risk. The result is predictable: exposures go unnoticed, remediation slows, and attackers exploit the gaps in between.
At TrollEye Security, we take a continuous approach. Our testing continuously validates exposures across your networks, applications, people, and vendors, while our platform makes remediation faster, clearer, and more efficient.
Supported by a long-term partnership approach, we help your team mature over time, turning ongoing collaboration into measurable security improvement.


Risk Reduced
Continuously identify and validate exposures ranging from technical vulnerabilities to dark web threats.

Secure your attack surface with testing that spans networks, applications, your human firewall and more.

Tools Consolidated

Reduce costs with a platform that consolidates ASM, DAST, SCA tools, and more.

Increase efficiency with a centralized location for managing exposures.

Lower friction with broad integrations, including Azure, AWS, Jira, GitHub, and more.

Compliance Streamlined

Easily meet requirements for frameworks like NIST and PCI DSS with continuous testing.

Show auditors assessment history with complete testing and remediation logs.
See What Our Clients Are Saying
Our clients’ feedback speaks volumes about the dedication and expertise TrollEye Security brings to every engagement. Across industries, security professionals trust us to provide seamless, proactive cybersecurity solutions that empower their teams and strengthen their defenses.




In my opinion, what sets TrollEye Security apart is their ability to communicate complex findings effectively. They were responsive and accommodating throughout the process. TrollEye is a trusted partner in our cybersecurity efforts, and I highly recommend them for their technical expertise and client-focused approach!

Our Threat Exposure Management Services
Our threat exposure management strategy combines the use of our four services to put your defenses to the test and build a program that identifies and reduces the risks that matter most. Each service is built on three key principles;
- Continuous Process - Gain continuous visibility with regular testing against set of common risks and attack vectors.
- Integrated Platform - Manage every service from our platform, centralizing visibility, streamlining remediation efforts, and consolidating toolsets.
- Partnership Approach - Get expert guidance directly from your security testers with monthly cadence meetings designed to support your needs.
Each one addresses a specific type of exposures that pose a threat to your organization, providing your security team with the continuous visibility and validation needed to ensure security.

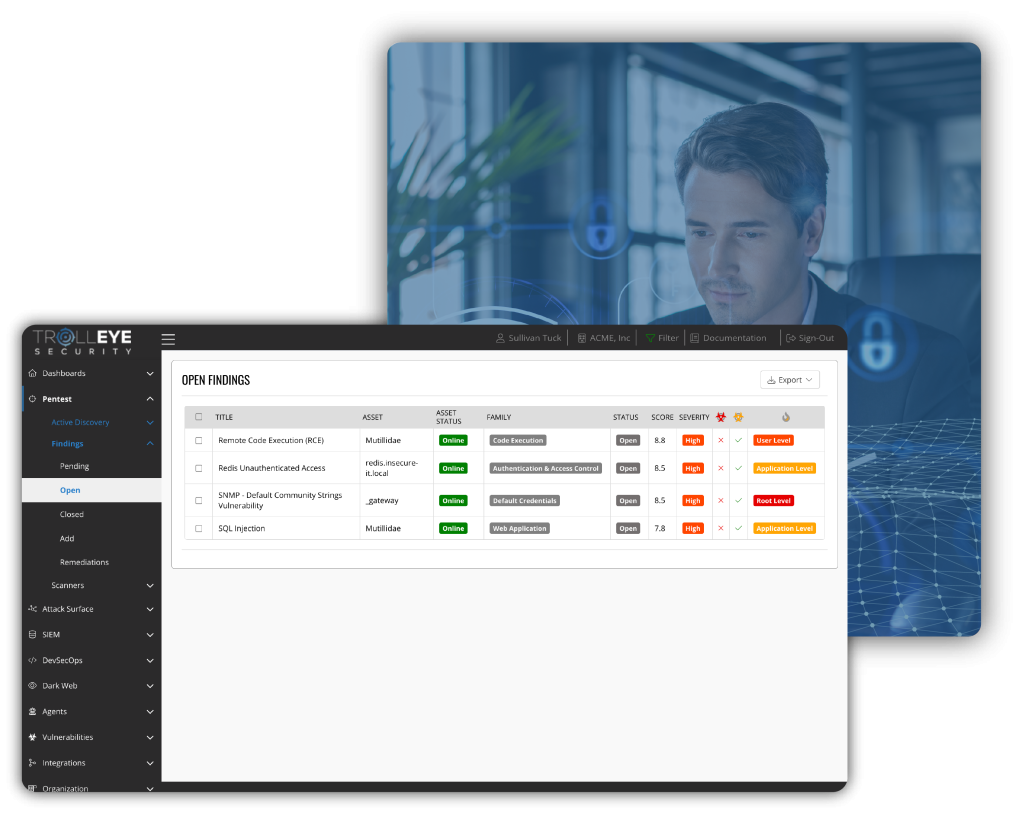
Penetration Testing as a Service (PTaaS)
Our Penetration Testing as a Service (PTaaS) delivers continuous validation of your defenses through up to weekly testing, real-time reporting, and direct collaboration with your security team.
From web applications and internal networks to phishing simulations and physical security testing, we provide broad testing that delivers actionable insight every-time.
Dark Web Analysis
Our Dark Web Analysis service uncovers hidden risks by monitoring dark web forums and marketplaces for your compromised credentials, vendor breach records, and executive data exposure.
Monthly scans and validation help your team focus on actionable threats so they can secure accounts, identify breaches, and improve defenses.

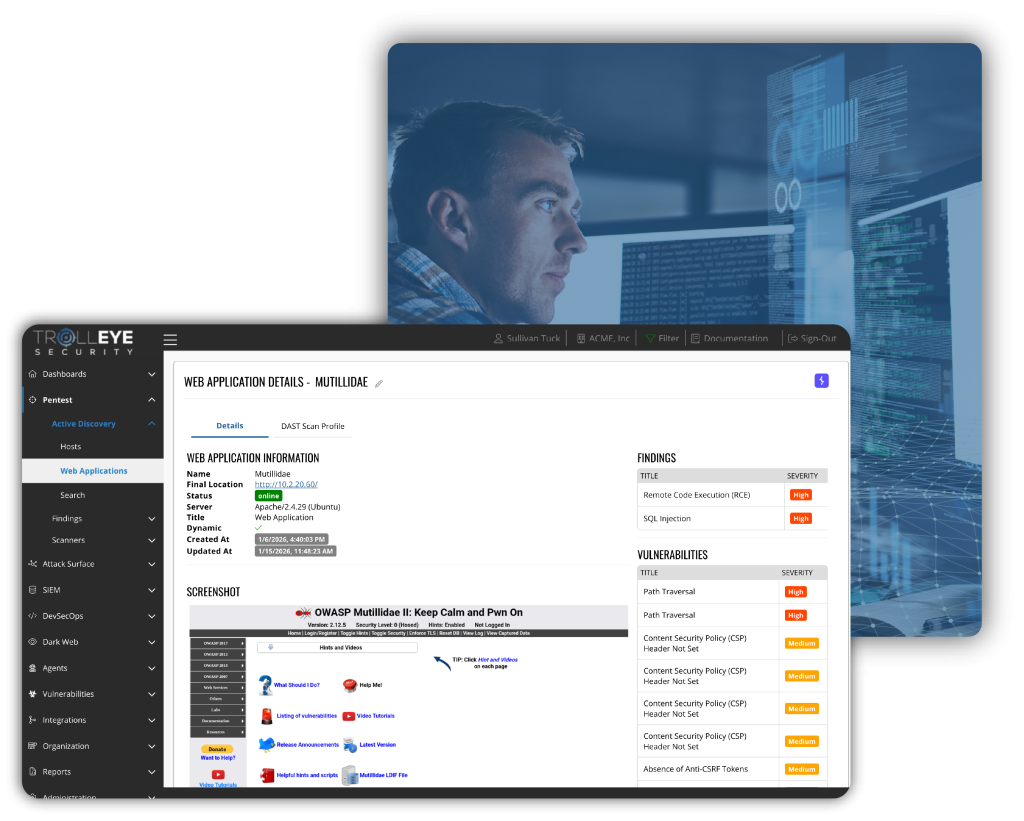
DevSecOps as a Service
Our DevSecOps as a Service integrates security directly into your development lifecycle, ensuring vulnerabilities are identified and resolved before code reaches production.
By embedding security into every phase of the SDLC, from Threat Modeling to DAST, we enable your organization tp accelerate delivery while maintaining secure, more reliable software.
Managed SIEM & Purple Teaming
Our Managed SIEM & Purple Teaming offering combines continuous monitoring with active adversarial testing to validate and strengthen your detection and response capabilities.
Through 24/7 threat visibility and coordinated purple teaming engagements, we help your team identify exposures and refine defense strategies continuously.

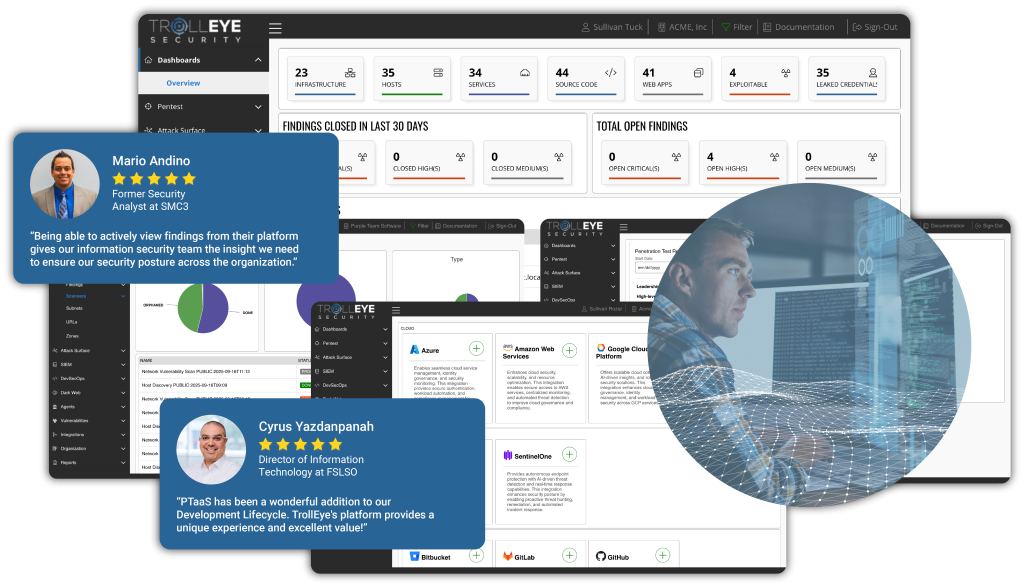
A Unified Platform for Efficient Exposure Management
At the core of our approach is a unified platform that centralizes exposure management and drives measurable risk reduction.
It connects every stage of testing, validation, and remediation in one environment, giving security teams complete visibility and control across their attack surface.
Get the Right Findings to the Right People
Role-based task distribution ensures findings reach the right people with the right context, accelerating remediation and keeping teams focused on meaningful progress.
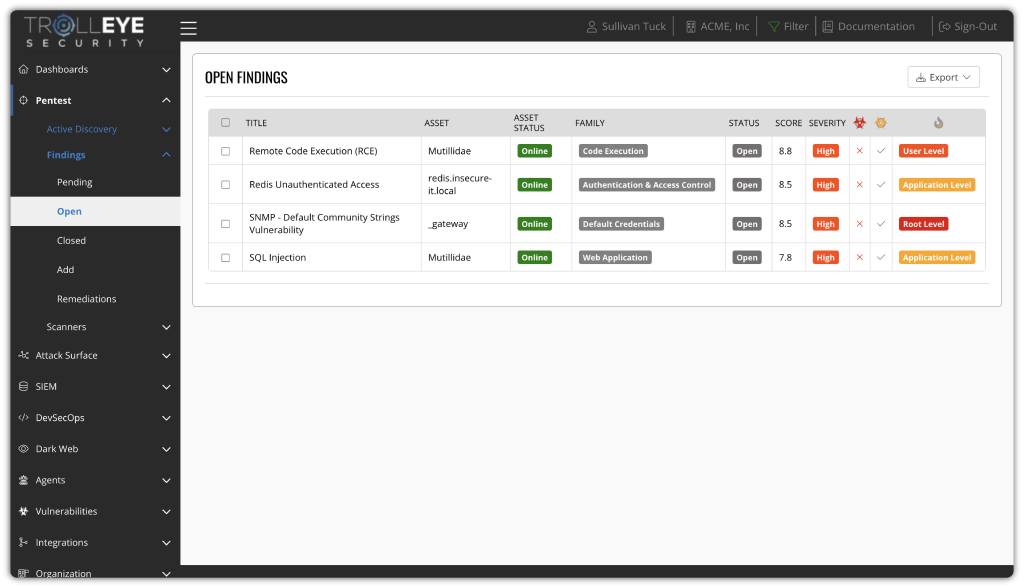
Unify Security Capabilities, Eliminate Fragmentation
By bringing together ASM, SAST, DAST, SCA, Dark Web Monitoring, and SIEM into a single platform, you eliminate tool sprawl and fragmented visibility, enabling unified threat detection, faster validation, and streamlined remediation from one place.

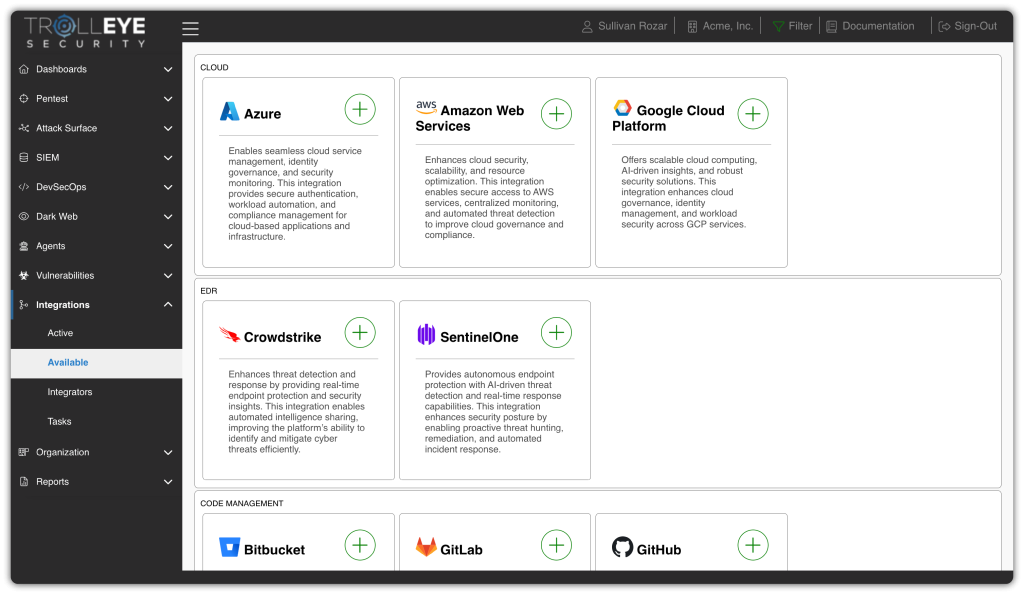
Connect Your Ecosystem Without Disruption
With broad integrations across your existing security and development stack, our platform connects seamlessly with tools like Azure, AWS, Jira, and GitHub to unify visibility and streamline collaboration.
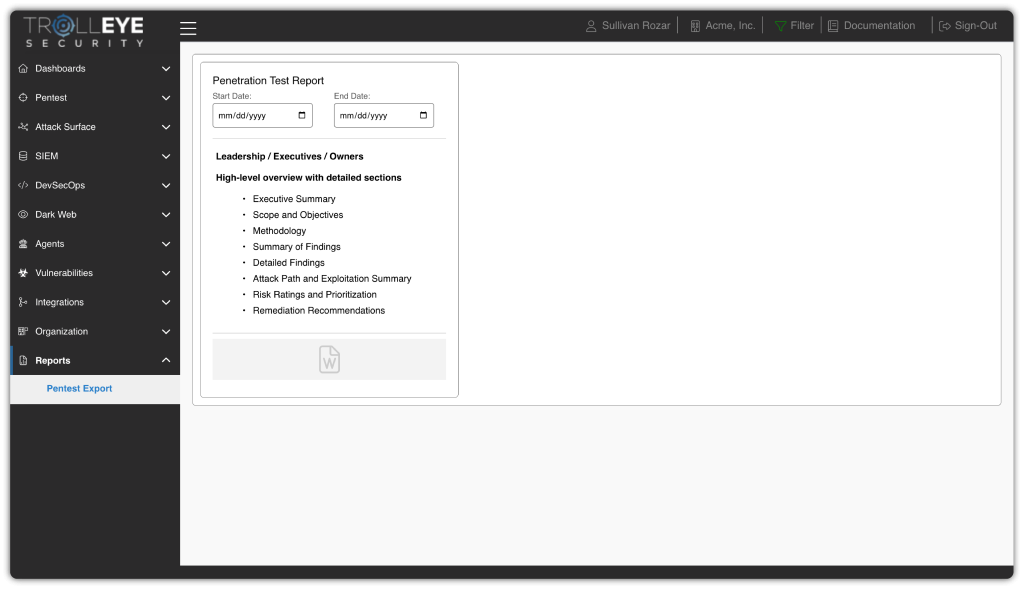
Simplify Audits and Strengthen Accountability
Automated compliance tracking and reporting make it simple to map findings to key frameworks like NIST, ISO, and SOC 2, reducing manual effort and audit fatigue.
Learn More with Our Resources
Use our latest resources, including white papers and case studies, to learn more about how you can use our services to help your security team continuously improve your security posture with the right information, the best tools, and expert guidance.

Download Crowdsourced Cybersecurity vs Penetration Testing as a Service (PTaaS)
Learn about the key differences between Crowdsourced Cybersecurity and PTaaS, including which testing approach is best for you.

Download Your Guide to Penetration Testing as a Service (PTaaS)
Learn what true PTaaS is and how it can help your security team reduce risk through continuous scheduled engagements.

Download Your Guide to Dark Web Analysis
Learn how Dark Web Analysis goes beyond traditional monitoring, and gives your security team insights into stolen credentials, vendor risk, and executive exposure.

Download Your Guide to DevSecOps
Learn how you can integrate security into the entire SDLC through DevSecOps, resulting in your organization producing more secure software, at a faster pace, cost-effectively.

Download Why SIEM Should Include Purple Teaming
Learn why SIEM should include purple teaming, and how your security team can remediate more vulnerabilities and stop more breaches by combining them.

Download Your Guide to Physical Penetration Testing
Learn how you can use physical penetration testing to identify gaps in your physical security, which is one of the most overlooked aspects of most cybersecurity strategies.

Download Enhancing Employee Training With Phishing Assessments
Learn how you can use phishing assessments to identify risks in your human firewall, and to improve your training program to reduce successful attacks.

Download What is Continuous Threat Exposure Management (CTEM) And How to Implement It
Discover how to turn Continuous Threat Exposure Management (CTEM) into a measurable, operational reality with our implementation guide today.

Download How Does TrollEye Enable Continuous Threat Exposure Management (CTEM)?
Discover how our process, platform, and partnership work together to turn CTEM into a living, measurable program with our guide to how we enable Continuous Threat Exposure Management (CTEM).

Download The Top Five Dark Web Threats & How to Mitigate Them
Learn about the top five threats shaping today’s cybercrime economy, why traditional dark web monitoring tools fall short, and how to turn dark web intelligence into real defense.

Why GBC Chose Our Red Teaming Assessments to Validate Their Security Posture
Let TrollEye Security Test Your Strength Before Hackers Do
Initial consultation
We’ll conduct a comprehensive analysis of your needs, networks, and assets to be tested.
MSA and RoE signed
The Master Service Agreement (MSA) and Rules of Engagement (RoE) cover all the details.
Testing and reporting
Threat exposure management begins, making your organization more secure with each engagement.
Hackers on your side
Ethical hackers tell cybercriminals, “Nice try. We already thought of that.”






















